Finding and fixing a broken cert for VCentre
I recently needed to add a cert to a vcentre 7.0 enviroment to allow Skyline and this is normally a striaght forward process. Certainly, 7.0 is many times easier than previous versions.
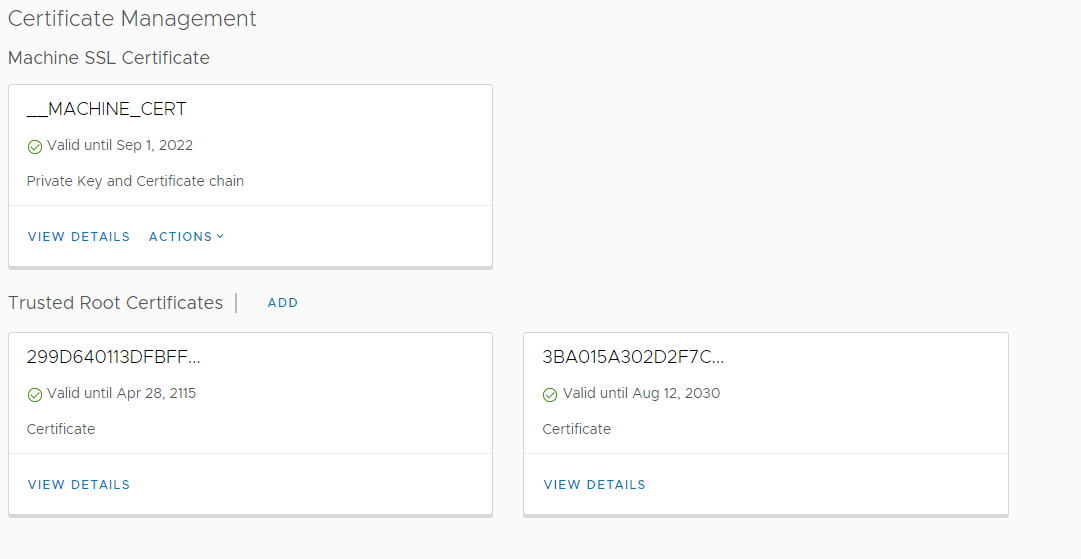
Adding the cert is just a case of going into vcentre -> menu -> administrator -> certificate management
If you're not familiar with certs then I need to quickly explain that certs are basically just files that contain cryptographic elements. For VCentre there are generally three files involved, there may be more if the certificate is issued by a sub CA (Certificate Authority). If the certicate is issued by a root CA then there are just thtee files involved, they would be:
CA Public Key
VCentre Public Key
VCentre Private Key
The CA's public key is required as the CA is the issuing body for that cert. The certs public key is required so that vcentre can pass that cert out to client endpoints and the key is required so that the data can be decrypted when it's recevived.
In VCentre, cert management is basically broken up into two sections, the first section is for the CA cert and the second is for the cert itself.
I suspect that most places will use an internal CA to generate the cert for VCentre and this is perfectly fine, there really is no difference between an internal and an external cert except for how many clients the trust model covers. In the case of an internal cert, only your internal clients should trust the CA.
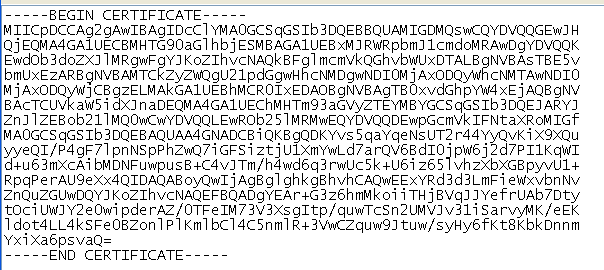
VCentre requires certs to be in a PEM format which is the standard for many cert generation tools - if you open up the cert file in something like notepad++ then you'll see something like this:
As long as it has the =BEGIN CERTIIFCATE= line you know you've got a PEM format cert and can continue.
Adding the root CA cert is just a matter of getting the public key (Which should be easily obtainable, it is designed to be public after all) and adding it to the cert management section.
Adding in the cert for vcentre itself needs the cert to be generated and then the public/private key exported in the previously mentioned PEM format. If you are doing this using a windows CA then you might end up with a PFX format cert. Windows, liking to be different, thinks that all clients will be windows and so doesn't provide any option to obtain a pem format. Not an issue as there are two ways to convert it. The easiest is via SSL shopper.
If you are not keen on giving your cert to a remote site and allowing them to do the conversion then you can do the change yourself if you have access to OpenSSL which is a standard linux tool. If you have the Windows Subsystem for linux then you can use that as well.
The command in OpenSSL to convert a PFX to PEM format is
openssl pkcs12 -in clientssl.pfx -out clientssl.pem -clcerts
openssl pkcs12 -in clientssl.pfx -out root.pem -cacerts
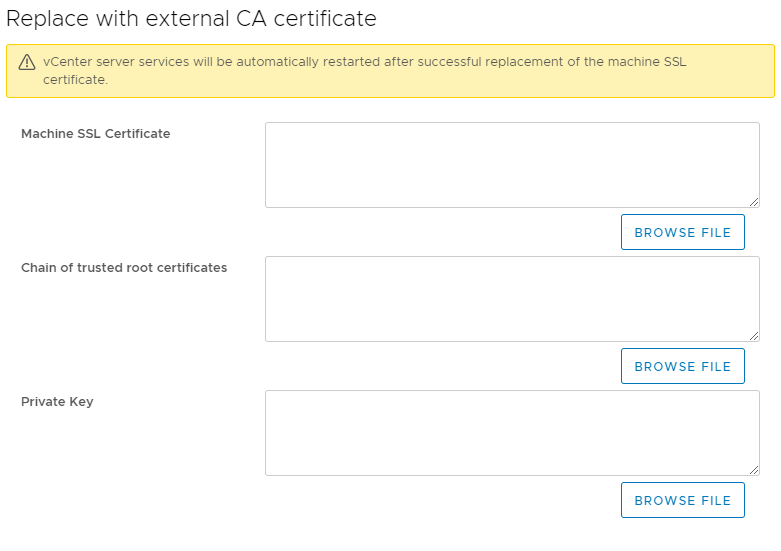
Now that we have both parts of the certificate in the correct format it is just a matter of adding them to VCentre by clicking on the Machine Cert -> Import and replace certificate -> replace with external CA certificate which will give you this screen:
The first box needs the public part of the certificate and the last box needs the private key. The middle box, the one that says "chain of trusted root certificates" only needs the public key of the CA cert if you generated the cert from the CA or it needs the public key of the CA and sub-ca if you generated the cert from a sub-ca. I don't use a sub-ca in my environment but if you do then you just need the public key of the root CA and sub-ca in the same file, it would basically be a file containing two or more sets of == BEGIN CERTIFICATE == entries.
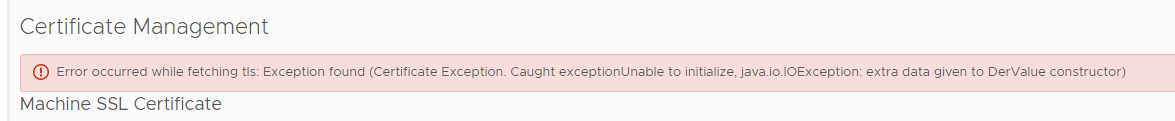
When I attempted to add the cert I'd generated I got a stnrage error.
I have to admit that this stumped me for a few days. I could not figure out why VCentre was rejecting my cert and as you can see, the error itself is not very descriptive. Even my searches for the error 'Exception Found (Certifcate Exception. Caught exception unable to initalize java.IOexception)' were not finding very much at all.
To cut a long story short I eventually decided to run the certs through openssl to see if it could spot any issues and that's when I discovered that one part of the vcentre cert itself was corrupt. I am not sure how this happened but I suspect that the cert was opened in notepad and notepad being the text editor that it is somehow mangled the format. Either way, the problem was pretty easy to fix as I just did a fresh export of both parts of the cert from the internal CA tool and this time VCentre accepted the three parts I needed and everything worked correctly.
Validating certs in openssl is quite easy to do and it's useful to know how to do it:
openssl rsa -in privateKey.key -check
openssl x509 -in certificate.crt -text -noout
If you're not familiar with certs then it is worth setting up a CA server and playing around with internal certs a little. I also published a vlog on setting up a basic external cert with Let's Encrypt which can be an easier way to start as you do not have to set up your own CA.
Subscribe to Ramblings of a Sysadmin
Get the latest posts delivered right to your inbox