Using PFSense as an internal CA
I think that by now it’s pretty clear that I’m in favour of HTTPS everywhere and one of the comments I’ve received from people is that “there isn’t any point in doing HTTPS on internal systems” which is something I totally disagree with.
Internal systems may get less traffic than external ones and it may only be from a select few users but it is negligent to treat internal systems with any less care than external ones just because it is on the internal network. Doing this just exposes your internal network to risk and promotes bad HTTPS behaviour in the form of statements such as “Just ignore that HTTPS error, it’s fine”. When you train people to ignore HTTPS warnings internally, you are training them to ignore then externally as well simply because most people will not understand the difference between a website that is internal and one that is external. Teaching good behaviour starts with ensuring that internal systems have the same protection as external ones.
Externally, I’m a fan of using Let’s Encrypt and setting up a cron job or scheduled task to renew the cert once a month or so. Internally and especially for lab environments I’m fine with using an internal cert server and a self-trusted certificate as long as the root CA is pushed out and included in the trusted certificate store of the client machines.
Many places that host internal certs use a Windows certificate service and I did the same for a few years but I found that Microsoft seemed to neglect their CA product and that it broke all too easily. It got to the point where I was spending more time trying to get the CA server to work than I was in actually issuing the certs.
A few months back I decided that enough was enough and that the lab windows CA server needed to be retired and replaced with something a little friendlier and less prone to breaking.
Having a look at the software installed in the lab I was actually surprised to see that two systems already had the ability to be a CA – FreeNAS and PFSense. As FreeNAS was already quite busy hosting various file services and, as PFsense is a security system, It made sense for PFSense to take on the role of CA.
Using the CA functionality in PFsense couldn’t be simpler, under System is a “Cert Manager” option and under there you just need to create the CA and then generate the certs from that:
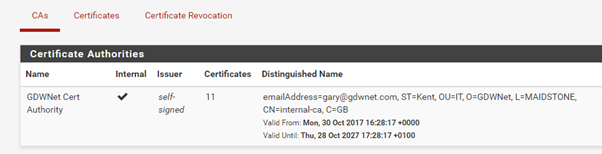
Because this is an internal CA, I don’t mind hosting my private keys, it’s certainly a lot more convenient and any compromise won’t affect anything external:
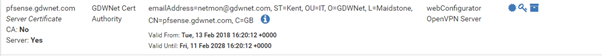
The only other thing to do is to send out the root CA to the various devices that need to trust it. On windows that can be done using a GPO and for Linux, I’ve included it in the build script.
One final thing to note, PFSense works great in a lab or production environment but in production environment there are licensing considerations to bare in mind.
Subscribe to Ramblings of a Sysadmin
Get the latest posts delivered right to your inbox